Sneaky Python Packages: Crypto Wallets Drained in New Malware Campaign
Data Breach and Crypto Theft: Who’s at Risk?
In a recent wave of cyberattacks, certain Python packages have been found to deploy malware with the only purpose of swiping sensitive info and crypto assets. The primary targets? Users involved with Raydium and Solana, based on Checkmarx’s latest report.
Sneaky Tactics: How the Attack Unfolded
Cybercriminals hit StackExchange users with a cunning ploy, masquerading as helpful contributors to threads. Their bait? A Python package dubbed ‘Raydium’ that harbored a multi-stage malware featuring a backdoor. This malicious campaign kicked off in late June with an innocent version on PyPI, but by early July, things took a dark turn.
The crooks launched several tainted versions of the “spl-types” Python package, setting their sights on crypto enthusiasts heavily invested in Raydium and Solana.
What is Raydium?
Raydium is a legitimate platform built as an Automated Market Maker (AMM) and liquidity provider on the Solana blockchain, supporting the Serum Decentralized Exchange (DEX). Interestingly, it lacks an official Python library, which makes this attack vector all of the more insidious.
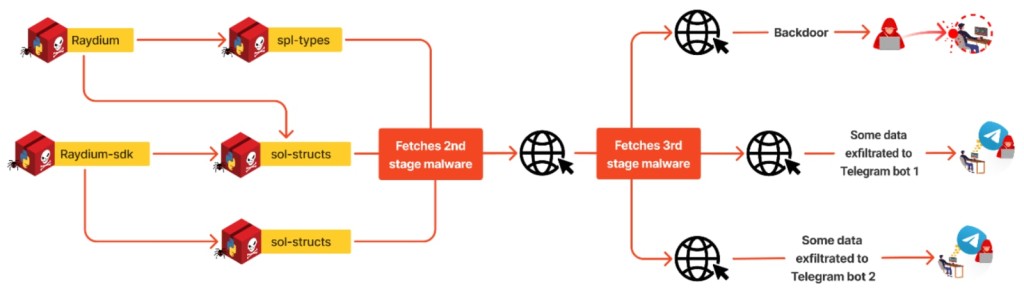
The Attack Mechanism: A Closer Look
Once the initial payload was deployed, it downloaded extra scripts from outside sources. These scripts scoured the victim’s system for sensitive data, compressing and shipping it off to the attacker’s command and control (C2) server through various Telegram bots.
One particularly sneaky file, init.py, was designed to run mechanically upon installation, stealthily exfiltrating a treasure trove of sensitive data while siphoning off crypto funds.
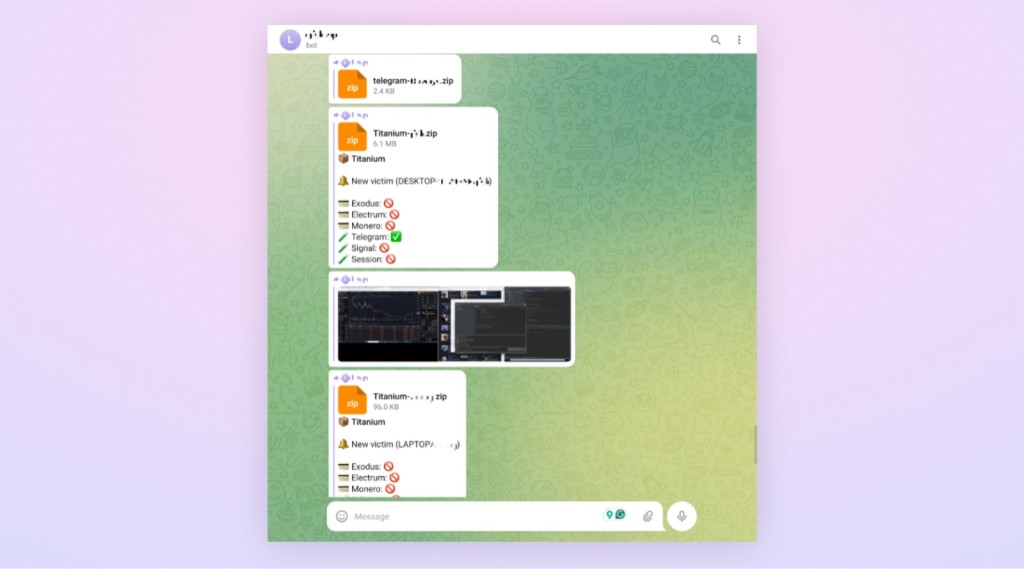
Exploiting Personal Data and Crypto Wallets
The attackers didn’t stop at crypto wallets. They harvested browser-stored details like bank cards, passwords, cookies, and browsing history, alongside data from messaging apps corresponding to Telegram, Signal, and Session. They even had the audacity to take screenshots of user activity.
Specific wallets like Exodus, Electrum, and Monero were also targeted, with the malware looking for out files containing crypto-related keywords and other crucial data, corresponding to GitHub recovery codes and BitLocker keys.
Detection Evasion and Persistent Threats
Sadly, Windows Virus and Threat Protection fell short in spotting this malware, which retained a backdoor for ongoing distant access. The persistent threat posed by this malware highlights the necessity for enhanced security measures.
Broader Implications
It’s not only Python packages under threat. Recently, there’s been a surge in hackers exploiting YouTube channels for crypto scams, deploying info-stealers like Vidar through fake software tutorials and bogus crypto giveaway ads.
Meet the Author
Lore Apostol, a cybersecurity news author at TechNadu, brings a pointy eye for detail along with her background in journalism and promoting. She values accuracy, brevity, and factual reporting while maintaining with the most recent trends in cybersecurity. Lore began her profession at TechNadu as a creative proofreader before transitioning to writing about cybersecurity.
Image Credit: www.technadu.com
