PyLoose: The Fileless Malware Hijacking Cloud for Cryptomining
There’s a sneaky latest player within the cyber world—PyLoose, a fileless malware targeting cloud infrastructures to use their processing power for Monero cryptocurrency mining. This digital intruder is actually a simple Python script that packs a punch with its encoded XMRig miner, a well-liked open-source tool often misused for cryptomining by leveraging CPU power.
Stealth and Evasion: The Art of Fileless Malware
The folks over at Wiz have been closely monitoring PyLoose, noting its clever tactic of executing directly from memory, making it a tricky nut for security systems to crack. Fileless malware like PyLoose is notorious for leaving no trace on a system’s harddrive, sidestepping traditional detection methods and using legitimate system utilities to embed harmful code into real processes.
Discovery and Impact
First spotted by Wiz’s security team on June twenty second, 2023, PyLoose has already compromised around 200 systems. According to their findings, this malware represents the primary documented instance of a Python-based fileless attack on cloud environments. Quite the groundbreaking feat, albeit for all of the fallacious reasons.
Unraveling the PyLoose Attack Chain
How does PyLoose make its move? It all starts with having access to devices through unsecured Jupyter Notebook services, which regularly don’t properly limit system-level commands. The attacker then cleverly fetches the fileless payload from a Pastebin-like service using an HTTPS GET request, loading it directly into Python’s memory space.
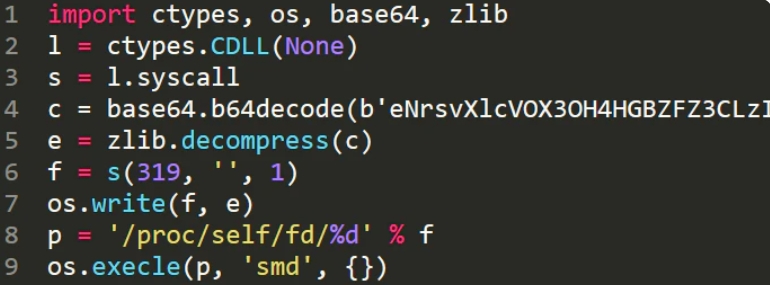 The PyLoose script (Wiz)
The PyLoose script (Wiz)
Once activated, the PyLoose script decodes and decompresses to inject the precompiled XMRig miner into memory using the “memfd” Linux utility. This method is a classic fileless technique on Linux systems, allowing the malware to execute without touching the disk.
“Memfd” is a Linux feature that Wiz explains can create anonymous, memory-backed file objects useful for things like inter-process communication. Attackers can then execute commands on this memory area as if it were an everyday disk file, launching latest processes and staying under the radar of most security measures.
Who’s Behind PyLoose?
Despite their thorough investigation, Wiz couldn’t pin the PyLoose attacks on a selected threat actor, because the intruders were careful not to depart any identifying traces. The team noted, nevertheless, that this adversary is not any rookie and seems to operate with a sophistication that sets them aside from typical cloud attackers.
Protecting Your Cloud Environment
To safeguard against threats like PyLoose, cloud administrators should ensure their services should not publicly exposed to potential exploits, implement strong password policies and multi-factor authentication, and restrict system commands to stop unauthorized code execution.
Stay Ahead of Emerging Threats

Want to maintain your corporation secure from the most recent cyber threats? Learn how cloud detection and response (CDR) can provide your security team the upper hand with this practical, no-nonsense guide.
Get the Guide
Image Credit: www.bleepingcomputer.com
